If you use a computer, you may be familiar with the terms “Trojan Horse virus,” “Trojan virus,” or just “Trojan.” Encountering Trojan viruses on a Mac can raise concerns about system security and performance. It’s important to know how to remove these threats effectively in order to keep your Mac safe and running smoothly. This guide offers detailed steps and strategies for users to detect, remove, and protect against Trojan virus on their Mac devices, ensuring a secure computing experience.
What Are Trojan Virus?
A Trojan virus, commonly referred to as a Trojan Horse, derives its name from the analogical link to the Wooden Horse of Troy. Just like the wooden horse was used to trick Troy’s defenses and permit enemy soldiers into the city, a Trojan virus masks itself as a legitimate application to fool users into downloading it. These viruses often present themselves as software updates, such as for Adobe Flash, or as antivirus programs.
How Do Trojan Work?
Trojans do not replicate on their own; instead, most attacks involve deceiving the user into downloading, installing, and running the malware. For instance, a hacker might send an email with a Trojan installer, using social engineering techniques to persuade you to open the attachment. If you do so, your device will download and install the Trojan. You may be familiar with phishing scams, where fraudsters use emails that appear to come from legitimate businesses. Hackers can employ comparable strategies to distribute Trojans.
How Do Trojan Virus Infect Your Mac?
You might be aware of Trojans, which often come disguised as email attachments. Even though these emails seem legitimate, their true purpose is to deceive you into opening the attachment or clicking on a harmful link, which would quickly infect your Mac with a Trojan. The key characteristic of Trojans is that you may not even recognize that you are installing them; they mimic real files and can introduce additional software or monitor your activities without your consent.
How Much Damage Can Trojans Do?
Believing the attachment to be genuine, you unintentionally downloaded and installed a Trojan. What are the consequences? The malware activates and begins to harm your computer, but the level of damage varies based on the hacker’s design of the Trojan. In general, Trojan malware can.
- Delete your important files.
- Install moew malware.
- Modify data.
- Copy data.
- Disrupt the device’s performance.
- Steal your personal info.
- Send messages using your email and/or mobile number.
When Is It Appropriate To Be Cautious About A Trojan On Your Mac?
The symptoms of Trojan horse viruses often resemble those of other types of viruses. Some of these symptoms include.
- Your Mac starts to behave oddly and perform unexpected tasks.
- Your Mac seems to be facing CPU overconsumption when it begins to run extremely slowly.
- Your internet connection becomes unstable and slow.
- You notice changes in the system options or browser configurations.
- Certain files and applications that you could previously access are now unavailable.
Keep in mind that discovering software on your Mac that you didn’t intend to install is a clear indication of a Trojan virus. This could manifest as an extension for your web browser or as an application in your Applications folder.
How To Remove Trojan Virus On Mac?
Use The Cleanup My System App
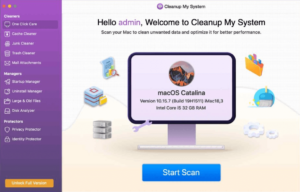
If you’ve observed unusual behavior on your Mac, it’s important to conduct a comprehensive malware scan. A highly recommended approach is to use a dedicated software like Cleanup My System, which can detect and remove a wide range of threats, including worms, ransomware, spyware, and adware, making it far more efficient than typical Trojan virus cleaners. Below are the steps to follow.
- Press the download button below to obtain the Cleanup My System application.
Note – Install the software on your computer after carefully reviewing the on-screen instructions and agreeing to the license terms.
- Begin the system cleanup by double-clicking the shortcut that has been created on your desktop.
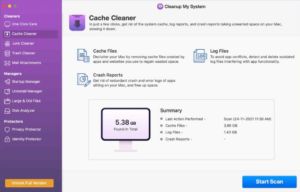
- Choose the Cache Cleaner option from the left panel. This feature will identify log files, crash reports, and cached data.
- Press the Start Scan button now. The Cleanup My System application will begin scanning your Mac for files that may not be needed.
- Once the scanning is complete, you can examine the scan results to find out what was identified in each sub-category. Afterward, choose the files you wish to delete and click on Clean Now.
Note – You can check the amount of space that software crash reports, unnecessary logs, and cache files occupy by viewing the area to the right of the Clean Now button.
Delete Malicious Profiles
Some Trojan viruses create additional profiles and use them to alter system and browser settings. Therefore, the first step is to check for any newly added profiles and delete any that are harmful. Here’s how you can do this.
- Go into System Settings.
- Go to the Users & Groups page.
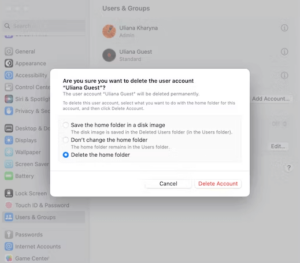
- Click the “i” next to any profiles that you did not set up, and select “Delete Account.” In the pop-up menu, choose “Delete the home folder.”
To delete each profile, simply follow the same steps.
Remove Malicious Applications
You can use Cleanup My System to fully uninstall applications from your Mac easily with just a few clicks. However, if you prefer to remove unknown apps manually, you will need to follow these steps.
- To uninstall the harmful application, first go to the Applications folder.
- Find the app and move it to the Trash, then go ahead and empty the Trash.
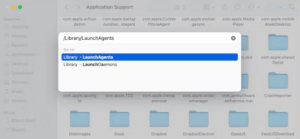
- Next, remove any leftover files associated with the app. In Finder, click on ‘Go’ in the menu bar and choose ‘Go to Folder.’
- Enter each of the provided paths one at a time into the window that opens, and remove any related files by moving them to the Trash.
~/Library/Application Support
/Library/Caches/
~/Library/Caches/
~/Library/Internet Plug-Ins/
~/Library/Preferences/
~/Library/Application Support/CrashReporter/
/Library/LaunchAgents
~/Library/LaunchAgents
~/Library/Saved Application State/
/Library/Application Support
/Library/LaunchDaemons
- Clean your Trash and reboot your Mac.
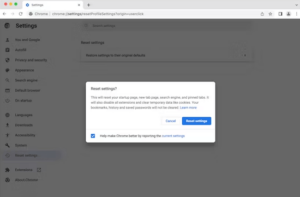
Reset Browser Settings
Restoring your browser settings to their original configuration can be a useful method for dealing with Trojan viruses that impact web browsers. This process returns the browser to its default state, removing any harmful alterations made by the Trojan. However, keep in mind that this may result in the loss of saved passwords, cookies, and browsing history. It’s advisable to back up important data before resetting your browser settings to prevent the loss of essential information.
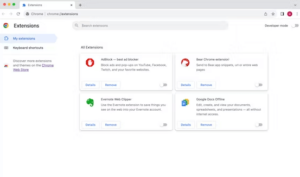
It is essential to remove harmful browser extensions when addressing Trojan virus that impact web browsers. Such extensions typically undermine browser security and compromise user privacy. Users can find and delete questionable or unwanted extensions by navigating to the browser’s settings or extensions menu.
Also, Take A Look At:
The Bottom Line:
By adhering to the detailed steps provided in this guide, users can successfully detect, remove, and safeguard their Mac systems from Trojan viruses. Using these strategies not only helps to eradicate current threats but also enables users to take preventive actions, ensuring their Mac devices remain secure and well-optimized against potential future infections.